The Complete Valuation Playbook for Data Security Businesses
A valuation guide to what data security companies actually sell for and the specific levers that push valuation higher.
If you run a data security company and you’re considering a sale in the next 1-12 months, valuation is not a mystery - but it is a game of pattern-matching.
Right now is a very “valuation-sensitive” moment in security: buyers are still doing deals, but they pay up mainly for assets that are clearly software-led, compliance-critical, and easy to scale. Services-heavy or “people-dependent” revenue still sells, but the multiple math is usually different.
This playbook is built from real private deal multiples, public market comps, and the premium vs discount drivers those deals reveal. It will show what data security businesses actually sell for, explain what pushes you to the high or low end, and give you a practical self-assessment and a 6-12 month action plan.
1. What Makes Data Security Unique
Data security is not one “category.” In buyer language, it’s a set of adjacent sub-sectors with very different valuation behaviors:
- Data Security SaaS: DSPM, DLP, data governance, recovery, secure collaboration - typically subscription software with high gross margins.
- Cloud-delivered security platforms: security delivered as a cloud service (often sold into broader security stacks).
- Encryption and cryptography infrastructure: HSMs, network encryptors, and cryptographic platforms - sometimes hardware-involved, sometimes software-heavy.
- Managed security and compliance services: SOC, GRC, incident response, audits - often people-heavy delivery.
- Backup and data protection platforms: cloud backup and recovery, often distributed through MSPs and channels.
Three unique valuation considerations show up over and over:
- Trust is part of the product. Buyers don’t just underwrite growth - they underwrite “will this break in a way that destroys reputation?” That changes diligence intensity and deal structure.
- Compliance is a revenue engine (or it isn’t). If your product is tied to regulatory requirements and audits, buyers see stickier renewals and lower churn risk.
- Distribution matters as much as features. In data security, a product with strong channel leverage (MSPs, cloud marketplaces, OEMs) can be worth far more than a better product with weak go-to-market.
Key risks buyers will always check (even if you’re growing fast):
- Security posture of your own environment (ironic, but critical): breach history, incident response readiness, and internal controls.
- Proof of “must-have” value: renewal behavior, expansion, and real-world outcomes.
- Customer concentration and procurement risk: a few big logos can be great - until one leaves.
- Deployment friction: heavy implementation and bespoke work tends to compress multiples.
2. What Buyers Look For in a Data Security Business
Most buyers - strategic acquirers and private equity - are trying to answer the same simple question:
“If we own this, will revenue be predictable and defensible, and can we scale it without scaling headcount at the same speed?”
The core “obvious” factors still matter:
- Growth rate and pipeline quality
- Recurring revenue mix
- Gross margin and delivery model
- Retention (customers sticking around)
- Clear path to profitability (or already profitable)
But data security has extra nuance. Buyers pay close attention to:
- Where you sit in the security stack: Are you a “nice-to-have dashboard” or a control point that blocks risk?
- Compliance and audit pull-through: Do customers buy because they must pass audits, reduce risk exposure, or meet standards?
- Time-to-value: How fast a customer gets live, and how hard it is to replace you.
- Integrations that create lock-in: identity providers, cloud platforms, SIEM/SOAR tools, data stores, M365/Google Workspace, etc.
How Private Equity Thinks (in plain English)
Private equity (PE) tends to buy with a 3-7 year horizon. They care about:
- Entry multiple vs exit multiple: If they pay 5.0x today, can they sell at 6.0x later by improving the business?
- Who they can sell to next: larger PE funds, strategics, or occasionally public markets.
- What levers they can realistically pull:
- Pricing and packaging cleanup
- Improving renewals and expansion
- Shifting services into repeatable “productized” offerings
- Cost discipline and automation
- Add-on acquisitions (if your category supports it)
In data security, PE gets most excited when the business looks like software (high gross margin, high recurring revenue), even if EBITDA today is modest - because the playbook to improve profitability is clearer.
3. Deep Dive: Software vs Services - The Valuation Fork in the Road
If there’s one valuation “fork” that dominates data security outcomes, it’s this:
Do you scale like software, or do you scale like a services firm?
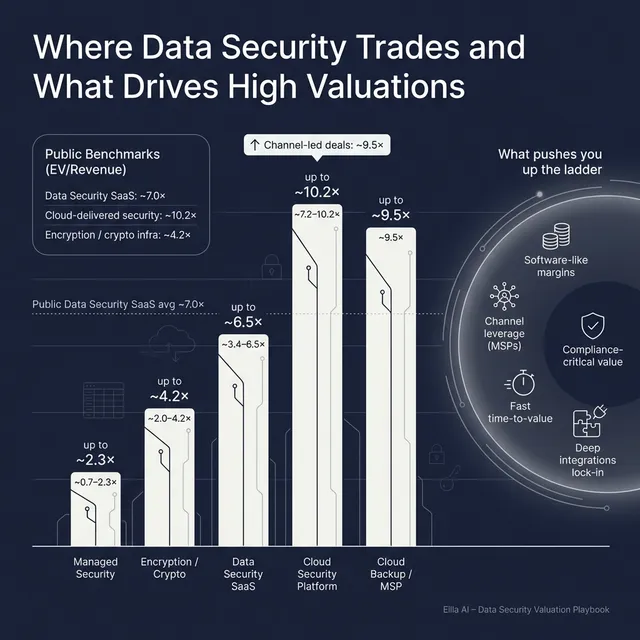
This shows up clearly in the deal data. Services-heavy cyber businesses tend to transact at modest revenue multiples: examples in the precedent set include deals around 0.6x to 2.4x EV/Revenue in managed security and consulting-like businesses. Meanwhile software and platform-like deals can clear much higher ranges, including 3.4x to 6.5x for enterprise cyber software/SaaS deals and around 9.5x for cloud backup/MSP platform transactions in the dataset. (These are group-level patterns, not “rules.”)
Buyers care because services revenue is often:
- Dependent on specific people
- Harder to scale without hiring at the same pace
- Less predictable in margins and renewal behavior
Whereas software revenue is often:
- More repeatable
- Higher gross margin
- Stickier when integrated into workflows and compliance
A simple way to self-diagnose:
How to move rightward (without pretending services don’t exist):
- Turn common implementation tasks into fixed-scope packages.
- Price services to encourage adoption, but make renewals and expansion software-led.
- Automate reporting, monitoring, and policy enforcement so “hours delivered” matters less over time.
4. What Data Security Businesses Sell For - and What Public Markets Show
Let’s separate two things:
- Private market deals show what real buyers paid for real companies.
- Public market multiples show what investors will pay for scaled businesses today - a reference band, not a private valuation guarantee.
The key takeaway from the data: your sub-sector and delivery model (software vs services) can swing multiples more than your feature set.
4.1 Private Market Deals (Similar Acquisitions)
Across the precedent transactions in the dataset, the group averages are:
- Overall: ~3.8x EV/Revenue and ~33.9x EV/EBITDA
- Enterprise cybersecurity software/SaaS: average ~6.6x EV/Revenue (median ~3.8x)
- Managed security services/consulting: average ~1.8x EV/Revenue (median ~1.6x)
- Cloud backup/MSP platforms: ~9.5x EV/Revenue (dataset cluster)
Here’s a founder-friendly way to interpret it:
These are illustrative ranges from the dataset. Your actual outcome depends on your growth, retention, margins, and deal process.
4.2 Public Companies
Public markets show wide dispersion in security. In the provided public set, some high-growth cloud security leaders trade at double-digit or much higher EV/Revenue, while many scaled, profitable security vendors trade in mid-single digits. The dataset’s group averages (as of mid-to-late 2025) are helpful reference points:
- Data Security SaaS (DSPM/DLP/Governance/Recovery): average ~7.0x, median ~5.6x
- Cloud-delivered security platforms: average ~10.2x, median ~7.2x
- Encryption/crypto infrastructure: average ~4.2x, median ~2.0x
- Managed security services/compliance: average ~3.0x, median ~1.0x
Two important interpretations:
- Public multiples are a ceiling and a compass, not a price tag. A private company is smaller, less liquid, and often riskier - so buyers typically apply a discount versus public comps.
- Scarce, strategic assets can break the “discount rule.” If you are a must-have puzzle piece for a strategic buyer, they may pay above what your size alone would imply (especially if synergy is real and near-term).
5. What Drives High Valuations (Premium Valuation Drivers)
Here’s what the dataset repeatedly associates with premium outcomes - grouped into themes you can actually act on.
5.1 Software economics that feel durable
Premium outcomes skew toward software-first models with high gross margins and low delivery friction. The dataset commentary points to strong investor appetite for scalable, predictable software cash flows, especially when tied to recurring revenue and clear renewal mechanics.
Practical founder examples:
- Your product is multi-tenant SaaS with low cost of service.
- You can show gross margin stability over time (not “this quarter was weird”).
- Services exist, but they don’t drive the core margin story.
5.2 Enterprise-grade contracts tied to compliance and “must-have” risk
Deals and comps that lean into compliance-critical workloads tend to get more confident underwriting. The pattern is simple: if customers buy because they must (regulation, audit, real breach risk), churn is usually lower.
What buyers want to see:
- Multi-year terms, renewal history, and proof customers treat you as mandatory.
- Credibility against standards (for example: GDPR alignment, ISO 27001 processes), and how that reduces buyer fear.
5.3 Category leadership and strategic fit
Strategic buyers pay more when your product clearly strengthens their platform. In the dataset, large strategic acquisitions explicitly cite portfolio fit and synergy rationale as justification for the price.
Founder translation:
- You can articulate “why you” and “why now” for a short list of acquirers.
- You have integrations, deployment patterns, and packaging that makes you easy to attach to a bigger platform.
5.4 Channel leverage (MSPs, cloud marketplaces, OEM bundles)
The dataset highlights premium revenue multiples in cloud backup and MSP-focused models, where distribution creates defensibility and scale.
In practice, channel leverage looks like:
- Partner-sourced ARR becoming meaningful (and measurable).
- A repeatable co-sell motion where partners keep bringing you deals.
- Low churn because you’re embedded in an MSP’s stack.
5.5 Scale and growth velocity
Scale helps buyers underwrite long-term relevance. The dataset commentary notes that buyers can tolerate negative EBITDA when growth and trajectory support platform economics - but the bar is higher if you’re small.
You don’t need to be huge to benefit:
- Clear growth consistency (not “one big deal saved the quarter”).
- Land-and-expand proof: customers buy more over time.
5.6 Profitability, or a believable path to it
Even when buyers value you on revenue multiples, they still care about whether the model turns into profit.
The dataset shows EV/EBITDA premiums in cases where profitability (or profit conversion credibility) exists, even when EV/Revenue is not spectacular.
Founder translation:
- Show margin improvement trend and explain why it’s repeatable.
- Demonstrate pricing discipline and cost control without harming growth.
6. Discount Drivers (What Lowers Multiples)
Discounts usually aren’t about one fatal flaw. They’re about buyers feeling uncertain, and uncertainty gets priced.
Common discount patterns in this sector:
- Services-heavy mix: if revenue scales with headcount, you drift toward services valuation bands (often much lower EV/Revenue in the dataset).
- Unclear recurring revenue quality: “recurring” that is really re-sold projects, or contracts that can be cancelled easily.
- Customer concentration: one customer or one vertical dominating revenue without a clear mitigation plan.
- Hard deployments and slow time-to-value: if your implementation takes months and requires senior people, buyers fear churn and margin compression.
- Weak proof of stickiness: lack of renewal data, unclear retention, or customers not expanding.
- Security and compliance gaps in your own operations: weak controls, missing policies, poor documentation - buyers will treat this as existential risk.
- Over-reliance on founder: sales, product, and key relationships all run through you.
The important part: most of these are fixable, or at least explainable, within 6-12 months if you treat them like a pre-sale project.
7. Valuation Example: A Data Security Company
Below is a worked example to show how valuation logic actually gets applied.
Important disclaimers:
- The company is fictional.
- Revenue is fictional (USD 10.0m).
- The valuation ranges are illustrative - not investment advice or a formal valuation.
Step 1: The logic (plain English)
- Pick the right peer set. If your economics look like software (high gross margin, recurring contracts), buyers will compare you to software security cohorts, not services.
- Anchor to realistic private and public ranges. In the dataset’s valuation logic example, a sensible “core” band for a small, software-like security company with negative EBITDA was 3.5x to 6.5x EV/Revenue. That band triangulates between private enterprise security software ranges (3.4x-6.5x) and public data security SaaS references (often higher, but usually discounted for small scale).
- Adjust up or down based on evidence.
- Premium evidence: software-like gross margins, enterprise-grade contracts, compliance-critical use, strategic fit, channel leverage, clear growth.
- Discount evidence: services creep, weak retention proof, lack of distribution advantage, concentration, messy financials.
Step 2: Apply it to a fictional company
Meet “NorthGate Data Controls” (fictional):
- USD 10.0m annual revenue (mostly subscription)
- High gross margin (software-first delivery)
- EBITDA slightly negative today due to growth spend
- Mid-market and enterprise customers, some regulated
- Integrations into major cloud data stores and M365
- Light services for onboarding, not the core revenue engine
Now apply scenarios:
Why these differences can be real:
- The discounted case happens if the buyer sees “services business in disguise,” weak renewals, or concentration risk.
- The core range fits a software-like business with decent proof, but limited scale and no huge distribution advantage.
- The premium scenario needs strong evidence: multi-year enterprise renewals, clear compliance pull, partner-driven distribution, and credible strategic fit.
Step 3: What this means for you
Two companies can both be “USD 10m revenue” and have wildly different valuations because buyers are not buying your past - they’re buying the reliability and scalability of your future cash flows.
If you want to change valuation, you usually don’t do it by adding 10% more features. You do it by proving retention, reducing delivery friction, making revenue feel recurring, and making yourself strategically relevant.
8. Where Your Business Might Fit (Self-Assessment Framework)
Use this like a mirror, not a report card. Score each factor 0 / 1 / 2:
- 0 = weak or unproven
- 1 = decent but inconsistent
- 2 = strong and well-documented
How to interpret totals (rough guidance):
- High total: you’re closer to premium outcomes because buyers can underwrite the story confidently.
- Mid total: you’re in fair-market territory - strong deal process and positioning will matter a lot.
- Low total: you may still sell, but you should expect lower multiples unless you fix the highest-impact gaps.
9. Common Mistakes That Could Reduce Valuation
These are avoidable, and they show up in real processes constantly.
9.1 Rushing the sale
If you start a sale process before your numbers and story are ready, you’ll either:
- scare off the best buyers, or
- create leverage for buyers to retrade price later.
9.2 Hiding problems
Every real issue comes out in diligence. The only question is whether it comes out early (when you can frame it) or late (when buyers lose trust and cut price).
9.3 Weak financial records
Buyers don’t need perfection, but they need clarity:
- What’s recurring vs one-time?
- What are gross margins by product line?
- What does churn and retention look like?
If you can improve reporting in 6-12 months, do it - it directly impacts buyer confidence.
9.4 Not running a structured, competitive sale process
A structured, competitive process with an advisor typically leads to meaningfully higher purchase prices - research is often cited around 25% higher outcomes when a competitive process is run well.
Competition creates leverage. Leverage creates price.
9.5 Revealing what price you’re after too early
If you tell buyers “we’re looking for USD 50m,” you often kill price discovery. Many buyers will come back with USD 50.1m, USD 50.2m - not what they truly might have paid.
Let the market speak first.
9.6 Data security-specific mistakes
- Not documenting your own security controls: buyers will demand it, and weak controls create existential risk.
- Letting services creep become invisible: if your “software company” needs lots of custom work to retain customers, buyers will price you like services.
10. What Data Security Founders Can Do in 6-12 Months to Increase Valuation
You don’t need a reinvention. You need focused work on what buyers actually pay for.
10.1 Improve the numbers buyers trust
- Build a clean bridge of revenue: subscription vs services, churn, expansion, net retention (how much customers grow after buying).
- Show gross margin durability by product line.
- Create a credible path to profitability (even if you’re not executing it fully yet): pricing, support automation, partner-led delivery.
10.2 Make stickiness undeniable
- Tighten onboarding to reduce time-to-value.
- Move customers onto multi-year terms where possible.
- Create proof artifacts: renewal cohorts, case studies tied to audit/compliance outcomes, before/after risk reduction.
10.3 Shift the mix toward “software-like”
- Productize repeatable services into fixed-scope packages.
- Make services optional and priced to encourage adoption, not become the business.
- Invest in automation that reduces human delivery load.
10.4 Strengthen strategic positioning
- Map 20-50 likely acquirers and show exactly how you fit their product gaps.
- Build or deepen integrations that matter to those buyers.
- Create a simple narrative: “We protect X data in Y environments for Z regulated workflows.”
10.5 Build distribution leverage
- If MSP/channel is relevant to your segment, prove it with partner-sourced ARR metrics.
- If cloud marketplaces matter, show real pipeline and conversion from those channels.
- If OEM is plausible, start with co-sell and joint reference wins before chasing big contracts.
11. How an AI-Native M&A Advisor Helps
A strong M&A outcome in data security often comes down to two things: finding the right buyers and running a process that creates competition without creating chaos.
An AI-native M&A advisor can expand buyer reach dramatically by using data-driven matching across deal history, product adjacency, financial capacity, and likely synergy. More relevant buyers means more competitive tension, stronger offers, and a higher chance the deal closes even if one bidder drops.
Speed matters too. With AI-driven buyer identification, outreach, and faster creation of marketing materials and diligence support, initial conversations and offers can often be reached in under 6 weeks - much faster than manual-only processes.
And it’s not “AI instead of humans.” The best model is expert human advisors - the people who know how buyers think - enhanced by AI for scale, precision, and execution quality. The result is Wall Street-grade process quality without traditional bulge bracket costs.
If you’d like to understand how an AI-native process can support your exit, book a demo with one of our expert M&A advisors.
Are you considering an exit?
Meet one of our M&A advisors and find out how our AI-native process can work for you.




