The Complete Valuation Playbook for Identity Verification Businesses
A data-driven playbook for valuing identity verification businesses - showing what buyers actually pay for trusted outcomes, defensible capability and software-like economics.
If you run an identity verification business and you might sell in the next 1-12 months, your valuation is not just about “growth” or “profit.” It’s about trust, risk, and proof - and whether a buyer believes your product reduces fraud and compliance headaches at scale, without blowing up unit economics.
This playbook is built from real precedent deals and public market valuation patterns across identity verification, eKYC, IAM, fraud data, PKI, and services-heavy identity consultancies. It will show what identity businesses actually sell for, what drives higher vs lower multiples, and how to run a simple self-assessment and a 6-12 month action plan to move up the range.
Now is a particularly important time to think about valuation in identity verification because consolidation keeps accelerating across cybersecurity, fraud, onboarding, and compliance - and buyers are paying up for “must-have” capabilities, but discounting anything that feels like a commodity feature, a services-heavy project business, or a compliance risk waiting to happen.
1. What Makes Identity Verification Unique
Identity verification is one of the few software categories where buyers don’t just value “features” - they value outcomes (lower fraud, higher approval rates, stronger compliance) and risk transfer (the buyer wants to sleep at night).
Most businesses in this space fall into a few common models:
- Digital onboarding / eKYC SaaS: document verification, liveness, selfie match, fraud signals.
- Digital identity verification & KYC/AML platforms: broader orchestration across checks, vendors, watchlists, workflows.
- Fraud and identity intelligence networks: identity graphs, consortium data, device/behavior signals, risk scoring.
- IAM and enterprise identity security: access, privileged identities, workforce and customer identity layers.
- PKI and digital trust: certificates, signing, regulated trust services.
- Biometrics hardware + software (especially travel/border): integrated deployments, longer sales cycles.
- Services-led IAM consultancies: implementation, integration, managed services around identity stacks.
What makes valuation different here is that “revenue is not revenue.” Buyers will separate:
- Recurring vs project revenue (subscription and usage-based revenue tends to carry more value than one-off implementations).
- Proof of accuracy and compliance (your false accept/false reject rates, audit history, regulatory posture, and incident track record).
- Data and model defensibility (is this hard to copy, or can a competitor match you in 6 months?).
Key risk factors buyers will always check:
- Regulatory exposure (KYC/AML, privacy, biometrics rules, cross-border data transfers).
- Fraud performance and liability (who eats losses when fraud slips through?).
- Concentration risk (a single bank, telco, or marketplace driving most revenue).
- Vendor dependencies (if your “AI” is mostly 3rd party data and models, buyers will discount the IP).
- Security posture (identity businesses are high-value targets; security maturity affects both price and deal certainty).
2. What Buyers Look For in an Identity Verification Business
Buyers typically fall into two buckets, and they value different things:
Strategic buyers (identity platforms, cybersecurity vendors, payments, risk, onboarding, travel tech) care about:
- How your product fills a roadmap gap (liveness, doc forensics, AML screening, identity graph, privileged identity, signing).
- Whether they can cross-sell you into their base quickly.
- Whether your tech reduces churn in their core product (identity is often sticky when it sits inside authentication, onboarding, or transaction approval).
Private equity buyers care about:
- Predictable cash generation (or a believable path to it).
- Whether the business can scale without hiring 1:1 people per dollar of revenue.
- Whether they can sell the business in 3-7 years to a larger strategic buyer or larger PE fund.
How private equity thinks
PE is usually thinking: “If I buy at X multiple today, can I sell at the same or higher multiple later?”
They underwrite:
- Entry multiple vs exit multiple: If your revenue quality is messy, they assume the exit multiple could be lower.
- Who’s the buyer later: A strategic acquirer will pay more if your asset is differentiated and “must-have.”
- Levers they can pull:
- Pricing (especially on usage-based verification).
- Packaging (turning add-ons into premium tiers).
- Reducing services intensity (productizing delivery).
- Add-on acquisitions (buying smaller competitors or data assets to strengthen defensibility).
In identity verification, the common PE fear is simple: “Is this a real product company, or a project company wearing SaaS clothes?” That one question can move your multiple dramatically.
3. Deep Dive: The Biggest Valuation Nuance in Identity Verification
Product outcomes vs “checkbox features” - why it changes your multiple
In identity verification, buyers don’t pay the most for the longest feature list. They pay the most for provable outcomes that matter to regulated customers: lower fraud losses, higher approval rates, faster onboarding, and fewer manual reviews.
The deal data supports this: platforms positioned as regulatory-grade verification paired with strong profitability have cleared premium outcomes (for example, a profitable KYC/fraud platform transacting around ~7.9x revenue and ~18.5x EBITDA, and a data-driven identity/fraud business around ~3.6x revenue and ~10.6x EBITDA). Those are not “nice UI” premiums - they reflect confidence in outcomes and earnings power.
Buyers care because:
- Regulated buyers are allergic to risk. If your solution helps them pass audits and reduce fraud, the product becomes “budget-protected.”
- Outcome proof reduces buyer diligence fear. If you can show consistent performance across cohorts and geographies, the buyer worries less about churn post-acquisition.
- Outcome proof supports pricing power. If you can quantify fraud reduction or manual review savings, you can raise prices without losing customers.
How you move from lower-value to higher-value over time:
- Start reporting performance like a risk product: approval rate, fraud capture, manual review rate, false accept/reject.
- Build case studies with measurable before/after impact (even if anonymized).
- Standardize implementations so results are repeatable, not founder-dependent.
4. What Identity Verification Businesses Sell For - and What Public Markets Show
The headline truth: identity verification valuations vary widely because the category includes everything from services-led consultancies to scaled platforms with data moats. The right way to interpret multiples is to first place your business model into the right “bucket,” then adjust based on quality.
4.1 Private Market Deals
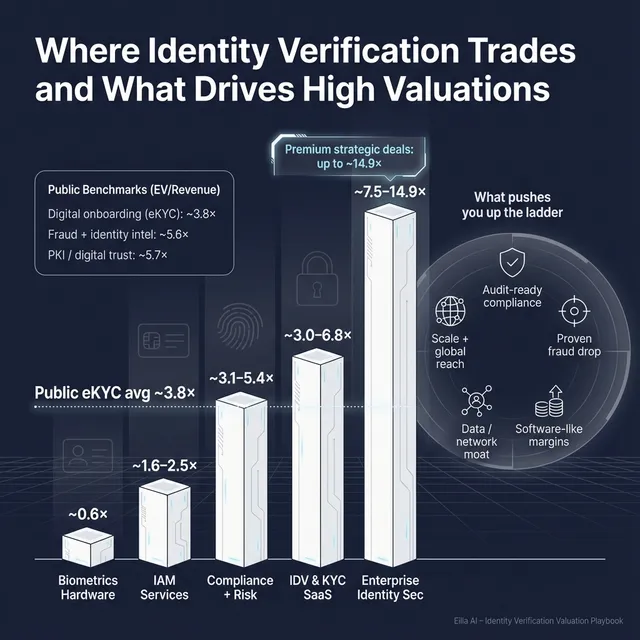
Across precedent transactions in and adjacent to identity verification, the grouped private deal data shows an overall average and median around ~4.8x revenue and ~17.5x EBITDA. But the range is driven by business model mix.
Here are the most relevant private ranges from the deal groups:
These are illustrative ranges, not a promise. The “same sector” can produce very different outcomes depending on recurring revenue, margins, defensibility, and customer concentration.
4.2 Public Companies
Public markets give you an “upper reference band,” but public multiples are not a private price tag. Scale, liquidity, and investor sentiment matter - and smaller private companies are usually valued at a discount unless they are strategically scarce.
As of mid/end-2025, grouped public trading multiples around identity and adjacent categories show:
How to use public multiples correctly:
- Treat them as a sanity check band, not a valuation answer.
- Adjust downward for smaller scale, lower margins, higher concentration, and less proven compliance posture.
- Adjust upward only when your asset is scarce (must-have tech, unique data, or category-defining outcomes).
5. What Drives High Valuations (Premium Valuation Drivers)
Premium outcomes in identity verification tend to cluster around a few repeatable themes. Importantly, buyers often pay up when these show up together - not just one at a time.
5.1 Regulatory-grade outcomes with real profitability
Buyers consistently reward identity platforms that can show:
- Audit-ready compliance behavior.
- Clear proof of risk reduction.
- Strong margins that look like software, not services.
In the deal data, regulatory-grade identity and fraud platforms with proven profitability achieved premium revenue and EBITDA multiples relative to services-heavy peers.
What you can do:
- Make “compliance outcomes” a measurable product output, not a marketing line.
- Present clean margin profiles by product line, not blended in a way that hides services.
5.2 Defensible verification capability (not just vendor orchestration)
Premium buyers pay more for defensible capabilities like:
- Liveness and presentation attack detection.
- Document forensics.
- AML screening integrated into workflows.
- Models and signals that improve with volume and data.
Deals in the data show acquirers paying up for advanced eKYC and fraud prevention capability even at modest revenue when the capability is strategic and productized.
What you can do:
- Show why your approach is hard to copy (data, models, integration depth, certifications, performance at scale).
- Reduce your dependency on third-party components where possible, or make vendor redundancy part of your story.
5.3 Software-led economics (high gross margin, operating leverage)
Premium multiples track software-like economics:
- High gross margins.
- Clear recurring revenue.
- Growth without linear headcount growth.
The contrast is visible in both public and private: software-led identity and security platforms trade far above services-led consultancies.
What you can do:
- Separate implementation revenue from recurring product revenue.
- Productize onboarding so services becomes a smaller percentage of delivery over time.
5.4 Mission-critical deployments with barriers to entry
In certain subsegments (notably travel/border biometrics), integrated hardware + software deployments can command strong EBITDA multiples because:
- Procurement and regulatory barriers are high.
- Replacement cycles are long.
- The solution becomes critical infrastructure.
If you are not in this niche, don’t pretend you are - but do borrow the principle: buyers pay for barriers.
5.5 Visible recurring growth (and deal structures that prove it)
Earn-outs tied to recurring revenue growth show up in higher-quality SaaS-style deals because they signal durability and align incentives.
What you can do:
- Build clear ARR reporting.
- Move contracts toward multi-year terms with renewal visibility.
- Track retention and expansion in a way that a buyer can trust.
5.6 Data-network moats
Identity intelligence businesses with proprietary data assets and network effects can hold premium value because:
- They are harder to replace.
- They reduce substitution risk.
- They often have stable margins.
What you can do:
- Build or partner into differentiated datasets.
- Be clear about data rights, privacy posture, and defensibility.
5.7 Scale and global reach
Scale reduces volatility. Global reach reduces concentration risk and expands buyer options. In the data, scale and global penetration correlate with stronger outcomes.
What you can do in 6-12 months:
- De-risk concentration (even modest diversification helps).
- Document international compliance posture and delivery capabilities.
Also don’t ignore universal valuation basics:
- Clean financials.
- Predictable revenue.
- Diversified customer base.
- A leadership bench that can run without the founder.
6. Discount Drivers (What Lowers Multiples)
Buyers don’t usually “hate” identity verification businesses. They hate uncertainty. Discounts happen when diligence reveals fragile economics, unclear defensibility, or hidden risk.
Common discount drivers in this sector:
- Services-heavy revenue mix: If growth requires adding people 1:1, you’ll get services multiples (often closer to the ~1.6-2.5x revenue band seen in IAM services comps).
- Commodity positioning: If you look like a replaceable vendor in a crowded doc/liveness market, buyers will push pricing down and reduce the multiple.
- Lack of proof: No clear reporting on performance, fraud impact, or compliance outcomes.
- Customer concentration: One big bank or marketplace can make revenue look strong but fragile.
- Negative gross margin surprises: For usage-based models, buyers will check unit costs aggressively (data, compute, human review).
- Vendor dependency risk: If your core capability is a third-party API, buyers may decide to build vs buy.
- Security and privacy gaps: Any weak security posture can become a price cut, a holdback, or a deal breaker.
- Messy contracts: Short terms, weak renewal rights, custom pricing without logic, unclear data processing terms.
The good news: many of these can be improved in 6-12 months with focused work.
7. Valuation Example: An Identity Verification Company
This is a fictional example to show how valuation logic works. The company, numbers, and scenarios are illustrative - not investment advice or a formal valuation.
Step 1: The logic (simple version)
- Pick the right comp bucket first (SaaS identity verification vs services-led identity consulting vs data network vs PKI).
- Start with a “core” multiple range from the closest private comps (because private buyers price private risk).
- Sanity check against public multiples, but don’t anchor on outliers driven by scale or platform economics.
- Adjust up or down based on premium drivers (outcomes, defensibility, recurring revenue, margins, scale) and discounts (services mix, concentration, weak proof, risk).
Step 2: Apply it to a fictional company
Meet VeriHarbor (fictional):
- USD 10.0m revenue
- 75% usage-based recurring verification revenue, 25% implementation/services
- Strong gross margin for the category, but still some manual review costs
- Customers: mid-market fintechs and marketplaces; no single customer above 15%
- Proven outcomes: documented reduction in fraud and manual review time
- Not a massive global platform yet, but clearly product-led
Given the private market identity verification and KYC/AML software platform band (roughly ~3.0-6.8x revenue in the grouped deals), a reasonable way to frame scenarios might look like:
Step 3: What this means for you
Two identity verification companies with the same USD 10m revenue can be worth very different amounts because buyers are not buying revenue - they’re buying trusted outcomes, defensible capability, and scalable economics.
If your business looks more like a services-led identity consultancy, the more relevant anchor is usually closer to the ~1.6-2.5x revenue band seen in IAM services transactions, not the SaaS platform bands. If you look like a data-network business or a scaled security platform, the ceiling can be much higher - but the burden of proof is higher too.
8. Where Your Business Might Fit (Self-Assessment Framework)
Use this as a quick, honest diagnostic. Give each factor a score:
- 0 = weak / not proven
- 1 = okay / partially proven
- 2 = strong / clearly proven
How to interpret your total (rough guide):
- High scores: you’re closer to premium outcomes in your segment.
- Middle scores: fair market range - a strong process can still produce a great result.
- Low scores: you may be leaving real money on the table if you sell immediately; focus on the biggest fixable drivers.
The goal isn’t to “get a perfect score.” It’s to identify the 2-3 improvements that will change how buyers bucket your business.
9. Common Mistakes That Could Reduce Valuation
Rushing the sale
If you go to market without a clear story, clean numbers, and a buyer-ready data room, buyers will price uncertainty. In identity verification, that often means discounts around churn risk, compliance risk, and gross margin sustainability.
Hiding problems
Problems will surface in diligence. When buyers discover issues late (security gaps, performance gaps, customer disputes), trust breaks and valuation drops - or the deal dies.
Weak financial records
Identity verification businesses often have messy COGS (data, compute, manual review) and blended services revenue. If you can’t explain margins cleanly by product line, buyers assume the worst.
No structured, competitive process with an advisor
A competitive process matters. Research and market practice consistently show that running a structured process with an advisor often leads to meaningfully higher purchase prices - on the order of around 25% - because it improves positioning, buyer reach, and negotiating leverage.
Naming your price too early
If you tell buyers “we want USD 10m EV,” you cap upside. Buyers will often offer USD 10.1m, USD 10.2m… instead of discovering what they would have paid in a real competitive process.
Industry-specific mistakes that hurt identity deals
- Not being crisp on liability (fraud losses, chargebacks, false accepts) and who bears them.
- Unclear privacy and biometric compliance posture (especially cross-border processing). Even if you’re fine, ambiguity alone can trigger discounts or holdbacks.
10. What Identity Verification Founders Can Do in 6-12 Months to Increase Valuation
Improve the “quality of revenue”
- Increase the share of recurring revenue (subscriptions, usage-based contracts with minimums).
- Move customers to multi-year terms where possible.
- Reduce services dependence by packaging implementation into fixed scopes and reusable modules.
Prove outcomes like a buyer would
- Build a simple “outcomes pack” per segment: fraud capture, approval rate lift, manual review reduction, time-to-onboard.
- Create 3-5 case studies with measurable before/after metrics.
- Standardize reporting so results are comparable across customers.
Protect margins and explain them clearly
- Break out COGS drivers: data costs, compute, human review, third-party vendors.
- Reduce manual review costs via workflow improvements (even small reductions can change buyer confidence).
- Present gross margin by product line, not just blended.
De-risk diligence
- Tighten security posture and documentation (identity buyers are sensitive here).
- Clean up data processing terms, subprocessors, and cross-border flows.
- Reduce customer concentration where possible (even one or two new logos can shift perception).
Build a buyer-ready narrative
- Position your business in the right category: outcome-led verification, data-network intelligence, platform workflow, or trust infrastructure.
- Be explicit about why you win and why it’s hard to copy.
- Show a credible 2-3 year plan that doesn’t rely on “hiring a lot more people.”
11. How an AI-Native M&A Advisor Helps
A strong exit outcome is usually less about “finding one buyer” and more about creating a market dynamic where multiple buyers see your business clearly - and compete.
Higher valuations through broader buyer reach: AI can expand your buyer universe to hundreds of qualified acquirers based on deal history, synergy fit, and ability to transact. More relevant buyers means more competition, stronger offers, and more options if one buyer drops late.
Initial offers in under 6 weeks: AI-driven buyer matching and outreach, faster creation of buyer-ready materials, and structured diligence support can compress the timeline from “getting organized” to real conversations and initial offers.
Expert advisory, enhanced by AI: You still need experienced human advisors to run the process, frame the narrative, and negotiate. The AI layer improves speed and coverage, while the advisory layer provides credibility and “buyer language” positioning - delivering Wall Street-grade process quality without traditional bulge bracket costs.
If you’d like to understand how our AI-native process can support your exit, book a demo with one of our expert M&A advisors.
Are you considering an exit?
Meet one of our M&A advisors and find out how our AI-native process can work for you.




