The Complete Valuation Playbook for Vulnerability Management Businesses
A valuation guide to what vulnerability management businesses sell for and what boosts multiples.
If you run a vulnerability management business, you already know the demand story is strong - attackers move faster, environments get messier (cloud, containers, SaaS, OT), and boards are less patient with “we scan and we have a PDF.”
What’s changing is how buyers price that demand. In the last few years, the gap widened between businesses that help customers find vulnerabilities and businesses that help customers actually reduce exposure in a repeatable, measurable way.
This playbook is a practical, data-based guide to (1) what vulnerability management businesses actually sell for, (2) what drives higher vs lower multiples, and (3) how to assess where you sit - plus a 6-12 month action plan to move up the valuation range.
1. What Makes Vulnerability Management Businesses Unique
Vulnerability management is not one “category.” Buyers quickly split the world into different business types - and they price them very differently:
- Platform-led vulnerability/exposure management: software that scans, prioritizes, and increasingly ties into remediation workflows.
- Attack surface management and exposure analytics: broader asset discovery + risk context (cloud, external, identities, configs), sometimes adjacent to VM.
- Managed vulnerability management (MVM): recurring services where you run the program (tools, tuning, reporting, ticketing, SLAs).
- Project-led services: pen testing, assessments, compliance-driven scans, remediation sprints.
That mix matters because vulnerability management has a unique valuation “truth”:
- Scanning is easy to buy. Fixing is hard to run. Buyers pay more for businesses that sit closer to “closed-loop remediation” (prioritization, ownership, ticketing, validation), not just detection.
- Trust and accuracy are product features. False positives, noisy reporting, and weak prioritization drive churn fast - and buyers know it.
- Data and integrations are the moat. VM lives inside a customer’s stack: ticketing (ServiceNow/Jira), cloud providers, endpoint tools, CI/CD, asset inventory. Tight integration increases stickiness and pricing power.
- You touch sensitive systems. Buyers always diligence security posture, permissions, data handling, and operational controls - because a VM provider that creates risk is a deal-breaker.
Key risks buyers will always check in this sector:
- Customer dependence on a few “hero” practitioners (delivery risk)
- Overreliance on one underlying scanner/data feed (vendor concentration risk)
- Evidence that customers don’t renew unless you discount (weak product value)
- Inconsistent results across customers (process maturity risk)
- Gross margin that can’t scale (services-heavy cost structure)
2. What Buyers Look For in a Vulnerability Management Business
Buyers tend to value vulnerability management businesses on two questions:
- How predictable is your revenue? Recurring contracts, renewals, and expansion matter more than a big pipeline slide. Buyers pay for confidence that next year’s revenue is already “mostly spoken for.”
- How differentiated is your outcome? “Better scanning” is rarely enough. Buyers want proof you reduce risk faster: fewer criticals open, faster time-to-remediate, lower exposure over time, fewer production incidents tied to known vulns.
Then they layer the classic fundamentals:
- Growth rate (especially in recurring revenue)
- Gross margin and path to margin improvement
- Customer retention (logos and dollars)
- Customer concentration (one customer can distort valuation)
- Sales efficiency (repeatable motion, not founder-only selling)
- A leadership bench that can run post-close integration
What strategic buyers are really buying
Strategics (security platforms, IT services groups, managed security providers) often buy VM businesses to:
- Fill a product gap in a broader security platform
- Add a recurring managed service line that increases customer stickiness
- Cross-sell into an installed base (the “I can sell this tomorrow” effect)
When a strategic can articulate clear cross-sell or portfolio fit, they can justify paying more - even if near-term profitability is not perfect.
How private equity thinks about it (in plain English)
Private equity (PE) cares about buying at one multiple and selling later at a higher multiple - but only if the business gets “cleaner” and more scalable.
Their typical logic:
- Entry multiple vs exit multiple: they want to buy you at a reasonable price and exit in 3-7 years to a bigger buyer (larger PE, strategic, or public market).
- What levers do they expect to pull?
- Raise prices where you’re underpriced relative to risk reduction delivered
- Improve renewals by tightening onboarding, reporting, and customer success
- Reduce services drag by productizing delivery and standardizing playbooks
- Add bolt-on acquisitions (especially in services-heavy VM programs)
- What scares PE? Customer concentration, founder-dependence, messy financials, and “revenue that looks recurring but behaves like project work.”
3. Deep Dive: The Valuation Nuance That Matters Most - “Find” vs “Fix”
The highest-impact nuance in vulnerability management valuation is this:
Are you paid for producing findings, or are you paid for running a program that gets vulnerabilities fixed?
This shows up everywhere in buyer behavior - and it explains why two businesses with similar revenue can sell at very different multiples.
Buyers pay more when:
- Your revenue is tied to ongoing outcomes (continuous scanning, prioritization, ticketing, verification)
- You are embedded in workflows (ITSM, CI/CD, cloud security, endpoint)
- You can prove measurable risk reduction (not just activity)
Buyers pay less when:
- Revenue is mostly one-off assessments
- The customer relationship is anchored to a few consultants
- Reporting is generic, noisy, or hard to act on
A simple way to think about it:
How to move right over time (without a massive pivot):
- Convert “assessment customers” into managed programs with a monthly fee and clear SLAs
- Standardize your remediation workflow (ticketing, ownership, validation) so outcomes are repeatable
- Build proof: baseline exposure at onboarding, then show improvement every quarter
- Reduce noise: tuning, prioritization, and asset context are not “nice-to-haves” in valuation - they are retention drivers
4. What Vulnerability Management Businesses Sell For - and What Public Markets Show
Here’s what the data actually shows: multiples are primarily a function of business model (platform vs services), recurring revenue quality, and defensibility.
In the sources you provided, private deals cluster around services-like multiples for services-heavy businesses and software-like multiples for productized platforms, with public markets generally setting a higher “ceiling” for scaled, high-margin software.
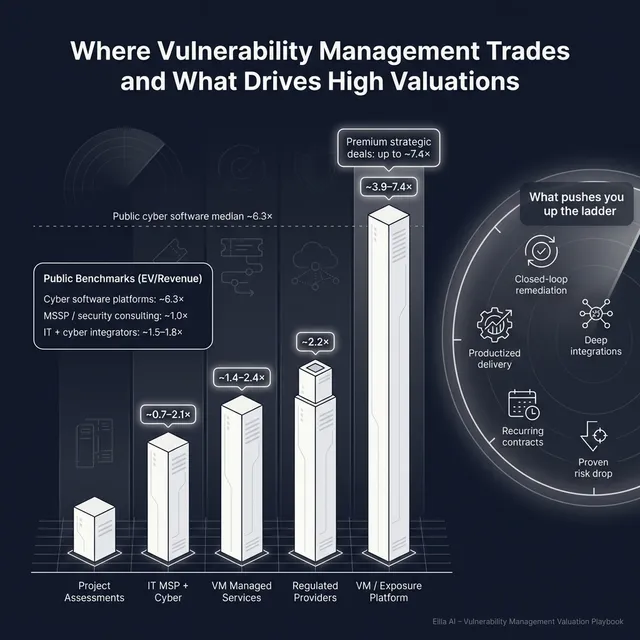
5.1 Private Market Deals (Similar Acquisitions)
A useful way to interpret private precedent deals for vulnerability management is to map your business to the closest “deal type”:
- Services-heavy cyber firms (pen testing, GRC, managed services) in the dataset cluster around ~1.4-2.1x EV/Revenue as a common band, with some deals pushing higher when there’s strong defensibility or regulated access.
- IT managed services with cyber offerings trend lower on average (~1.3-1.6x EV/Revenue) because buyers view them as people-and-utilization businesses.
- Software-led enterprise security platforms (including vendors with VM adjacent capability) show meaningfully higher revenue multiples in the deal set, commonly ~3.9-4.9x EV/Revenue, with premium outcomes in the dataset reaching into the ~6-7x EV/Revenue range when the asset is strategically important and product-like.
Illustrative private market ranges from the provided deal groups:
How to use this: treat these as illustrative reference bands, not a price tag. Your exact multiple depends on mix (recurring vs project), margin profile, customer stickiness, and how “platform-like” your differentiation is.
5.2 Public Companies
Public markets (as of mid-to-late 2025 in your dataset) generally reward scaled cybersecurity software platforms more than services businesses.
From the public group multiples provided:
- Cybersecurity software platforms (including vulnerability/exposure management and adjacent categories) trade around ~6.3x median EV/Revenue and ~8.0x average EV/Revenue, with ~21.1x median EV/EBITDA (higher on average due to outliers).
- Managed security providers and security consulting show a much lower ~1.0x median EV/Revenue, with a higher average driven by a few outliers.
- Regional IT and cyber integrators / managed IT trade around ~1.5-1.8x EV/Revenue and ~8-9x EV/EBITDA.
A simple public-market “reference map”:
How founders should use public multiples:
- As guardrails, not answers. Public comps set “what great looks like” at scale.
- Adjust down for smaller size and higher risk. Private businesses typically trade below public comps unless the asset is scarce and strategic.
- Adjust up if you’re unusually differentiated. If you have a real moat (regulated access, vertical dominance, or product-like economics), buyers can justify paying closer to software bands even at smaller scale.
6. What Drives High Valuations (Premium Valuation Drivers)
Premium outcomes in the data consistently show a few repeatable themes. Think of these as the levers that move you toward the top of your segment’s range.
1) Productized platform economics (even inside a services business)
Buyers pay more when they see scalable IP - not just great people.
- Examples founders recognize: proprietary prioritization logic, workflow automation, dashboards customers actually use, repeatable templates that reduce delivery hours.
- Why it matters: it raises gross margin, reduces churn, and lowers dependence on specific individuals.
2) Recurring revenue with improving margins
In the deal patterns, recurring managed security revenue tends to be valued more than project-led revenue - especially when gross margin is trending up.
- What to show: contract terms, renewal rates, expansion, and “cost to serve” improving over time.
- Founder-friendly example: “We used to spend 40 hours/month per customer; now it’s 20 because the process is standardized.”
3) Regulatory-grade compliance and governance credibility
Premium valuation narratives often appear when compliance and governance capabilities unlock enterprise or regulated buyers.
- What to show: certifications, audit-ready documentation, case studies that reduced audit pain or accelerated adoption.
- In VM specifically: tie VM to compliance outcomes (patch SLAs, control evidence, reporting cadence).
4) Defensible vertical specialization
Vertical focus shows up as pricing power and retention when it’s real (not just a slide).
- What “real” looks like: vertical-specific threat models, controls mapping, integrations, and reference customers.
- In VM: regulated verticals often value response times, reporting rigor, and change control discipline.
5) Strategic fit and synergy story that’s obvious
When a buyer can say “this immediately expands our platform or services footprint,” they can justify paying up.
- Your job: make synergies easy to believe - show integrations, partner channels, and a clear cross-sell path.
6) Identity/PAM adjacency (a valuation accelerant when credible)
Identity and privileged access are often treated as strategically scarce. Even if you’re a VM business, tight identity adjacency can lift perceived strategic value.
- Practical version: strong delivery partnerships, repeatable identity + VM packages, or light product modules that connect the two.
Also don’t ignore the “boring but valuable” premiums:
- Clean financials and predictable reporting
- Diversified customer base
- A leadership team that can run without the founder in every deal
- Clear KPIs: retention, margin, growth, and program outcomes
7. Discount Drivers (What Lowers Multiples)
Most “low multiple” outcomes aren’t because the sector is bad. They happen because buyers see avoidable risk.
Common discount drivers in vulnerability management:
- Project-heavy revenue disguised as recurring (month-to-month “retainers” that cancel easily)
- Low gross margin with no improvement path (custom delivery every time)
- Customer concentration (one or two large clients drive the business)
- High churn or weak expansion (customers don’t increase usage or scope over time)
- Commodity positioning (“we run scans” with no differentiated workflow or outcomes)
- Tool dependency (your value is mostly resale/implementation of someone else’s scanner)
- Founder or key-person dependence (especially in enterprise sales and delivery quality)
- Messy service profitability (no clarity on margin by customer or by service line)
- Security and compliance gaps (ironically common in cyber services) - weak controls, weak data handling, unclear permissions model
The good news: many of these are fixable in 6-12 months with focused execution.
8. Valuation Example: A Vulnerability Management Company (Fictional)
This example is fictional and designed to show how the logic works. The company, metrics, and valuation ranges are illustrative - not investment advice or a formal valuation.
Step 1: The plain-English valuation logic
- Start with business model match. If you’re services-heavy, use services comps first. If you’re software-like, use software comps.
- Triangulate a “core band.” Use multiple reference points (private services deals, public services comps, and software comps only if you truly look like software).
- Move the multiple up or down based on drivers. Recurring revenue, defensibility, margin trajectory, and strategic fit push up. Project dependence and risk push down.
Step 2: Apply it to a fictional company
Meet VulnBridge, a fictional vulnerability management business:
- USD 10.0m last-twelve-month revenue
- 70% recurring managed VM subscriptions (12-24 month contracts)
- 30% project services (one-off assessments and remediation sprints)
- 55% gross margin, 12% EBITDA margin
- Strong integrations into ticketing and cloud environments, but not a full standalone SaaS platform
Base case thinking (services-plus model): Given the data patterns for services-heavy cyber businesses, a defensible base band is often ~1.4-2.4x revenue when you are not a true high-margin SaaS platform, with upside if defensibility and recurring contracts are strong.
Premium case (more product-like): If VulnBridge had pushed to 85% recurring, materially higher gross margin, and clear product IP (repeatable modules customers pay for), it could start to justify a software-adjacent band similar to lower-to-mid enterprise security platform outcomes (~3.6-5.7x revenue in the provided reference set), assuming the product is real and retention is strong.
Discounted case (project-led reality): If renewal behavior is weak, margins are flat, and revenue is mostly project work, buyers tend to anchor closer to the lower services ranges (and sometimes below).
An illustrative “what that means” table:
Step 3: What this means for you
Two vulnerability management businesses can both have USD 10m revenue and still be worth radically different amounts.
The difference is not vibes. It’s:
- How recurring your revenue behaves in real life
- Whether your delivery scales without linear headcount
- Whether buyers believe your differentiation survives competition
- Whether outcomes are measurable and repeatable
9. Where Your Business Might Fit (Self-Assessment Framework)
Use this to be honest about where you sit today. Score each factor 0-2:
- 0 = weak / unclear
- 1 = okay
- 2 = strong / buyer-ready
How to interpret your total (rough guide):
- High band (mostly 2s): closer to premium outcomes within your segment
- Middle band: fair market, but you likely have 2-3 improvements that move valuation meaningfully
- Low band: consider delaying a sale if you can fix obvious issues in 6-12 months - the payoff can be large
10. Common Mistakes That Could Reduce Valuation
Rushing the sale
If you start a process before you can explain your numbers and story cleanly, buyers will price uncertainty - and uncertainty is expensive.
Hiding problems
Issues will surface in diligence. Hiding them breaks trust and often leads to repricing, harsher terms, or a dead deal. It’s almost always better to disclose early with a mitigation plan.
Weak financial records
This is especially costly in VM because buyers want to understand:
- Recurring vs project revenue clearly
- Gross margin by service line
- Customer-level profitability (who drains delivery time)
- Retention and expansion by cohort
Not running a structured, competitive sale process with an advisor
A single-buyer process rarely produces your best outcome. In practice, structured competition often leads to meaningfully better pricing - many advisors cite improvements on the order of ~25% versus “one buyer, one negotiation,” mainly because competition forces real price discovery.
Revealing what price you’re after instead of letting the market bid
If you tell buyers “we want USD 10m,” you often get USD 10.1m, USD 10.2m - not the real maximum they might have paid. Let buyers show their hand first.
Two vulnerability-management-specific mistakes that come up often:
- Selling “activity,” not outcomes: scans run, tickets created, reports delivered - but no proof exposure declines over time.
- Underestimating operational trust: weak access controls, unclear data handling, or sloppy permissions hygiene can spook buyers fast in this category.
11. What Vulnerability Management Founders Can Do in 6-12 Months to Increase Valuation
A) Make revenue behave more like recurring
- Convert top project customers into managed programs with clear SLAs and a monthly fee
- Extend contracts from month-to-month to 12-24 months where possible
- Introduce expansion hooks: additional asset classes (cloud, containers, OT), more business units, more integrations
B) Improve margins by productizing delivery
- Standardize onboarding, tuning, reporting, and remediation playbooks
- Track delivery hours per customer and reduce them systematically
- Package “repeatable modules” customers pay for (prioritization, validation, executive reporting, compliance mapping)
C) Prove outcomes buyers can believe
- Establish a baseline at onboarding (critical vulns open, time to remediate, asset coverage)
- Report quarterly improvement and tie it to your workflow
- Reduce noise (false positives) and show it improves customer experience
D) Reduce buyer risk before they ask
- Tighten security posture (access control, logging, policies, vendor risk)
- De-risk tool dependency (multi-tool capability, clear value-add beyond the underlying scanner)
- Improve customer concentration where possible (even one or two new mid-sized logos can change the story)
E) Get sale-ready operationally
- Prepare clean financial reporting and a simple KPI dashboard
- Build a data room that matches how buyers diligence VM (contracts, renewals, delivery model, security posture)
- Develop a crisp narrative: “why we win, why customers stay, how this scales”
12. How an AI-Native M&A Advisor Helps
A strong exit outcome in vulnerability management is often less about “the sector is hot” and more about running the process well - reaching the right buyers, telling the story with credibility, and creating competitive tension.
Higher valuations through broader buyer reach: AI can expand the buyer universe to hundreds of qualified acquirers based on deal history, strategic fit, and ability to pay. More relevant buyers means more competition, stronger offers, and a higher chance the deal closes even if one buyer drops.
Initial offers in under 6 weeks: AI-driven buyer matching, faster outreach, and rapid creation of high-quality materials can compress timelines. You can often get to serious conversations and early offers much faster than manual-only processes.
Expert advisory, enhanced by AI: The best outcomes still require experienced human advisors - but AI can raise the quality bar. You get professionally prepared positioning and materials that speak the buyer’s language, with the credibility that comes from advisors who’ve run these processes before - without traditional bulge-bracket costs.
If you’d like to understand how an AI-native process can support your exit, book a demo with one of Eilla AI’s expert M&A advisors.
Are you considering an exit?
Meet one of our M&A advisors and find out how our AI-native process can work for you.




